Google Chrome OS Developers made Critical Technology Decisions Based on my SANS Institute Research Paper.
If my research paper really did influence their decisions regarding an important technology, that is a very pleasant surprise. I could be reading this wrong, but it sure looks like my research paper, published by the SANS Institute clear back in 2002, may have directly influenced development decisions in Google's Chrome OS & Chromebook, and ongoing as recently as 2014. If it didn't directly influence the decision making process, it was still kind to have my paper as the reference link for the debate on the topic.
I've been concerned with the direction Google has been going over the years, but at least on this topic, kudo's to them for looking out for their end users, that would otherwise be severely vulnerable if using PPTP. They may "only be volunteer developers", and have the usual disclaimers, but since my paper is the number one web search result for this topic...
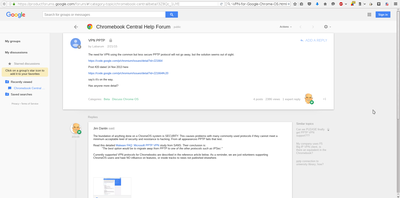
I am not the only one (by any means) to publish problems with the protocol, including Bruce Schneier and others. But it is nice they directly reference my research paper here https://productforums.google.com/forum/#!category-topic/chromebook-central/beta/I3Z8Qc_1UYE which was published on the SANS Institute website: Malware FAQ: Microsoft PPTP VPN (by Hawke Robinson).
The developer states: "The foundation of anything done on a ChromeOS system is SECURITY. This causes problems with many commonly used protocols if they cannot meet a minimum acceptable level of security and resistance to hacking. From all appearances PPTP fails that test. Read this detailed Malware FAQ: Microsoft PPTP VPN study from SANS. Their conclusion is: "The best option would be to migrate away from PPTP to one of the other protocols such as IPSec." "
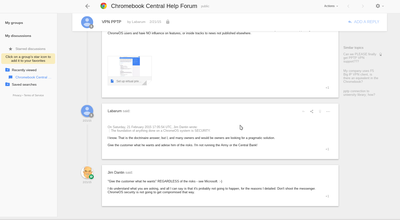
And in response to further urging, he responded with:
"I do understand what you are asking, and all I can say is that it's probably not going to happen, for the reasons I detailed. Don't shoot the messenger. ChromeOS security is not going to get compromised that way."'
Nice that all my efforts were not in vain.
To be clear, the above only validates that a volunteer developer cited my paper, but in the open source world, being run by mostly volunteers, and with none of the other developers refuting his statements to the user, and that the official OS still does not support this common protocol...
While Microsoft continued to deny, deny, deny, and keep exposing everyone to so many vulnerabilities, Google at least in this instance lived up to their old motto of "Don't be evil", and was looking out for their users.
Even somewhat recent listings about ChromeOS VPN features still indicate that they do NOT support PPTP: http://www.computerworld.com/article/2475853/cybercrime-hacking/a-chromebook-offers-defensive-computing-when-traveling.html "The least secure flavor of VPN is called PPTP and it is supported by most operating systems, including Windows 7, Windows 8, Android, iOS and OS X. Chromebooks do not support PPTP. " Computerworld | Feb 14, 2014 2:24 PM PT
And also: http://www.omgchrome.com/chromebook-ready-vpn-options-to-protect-your-privacy/ June 23, 2015 "Chrome OS lacks support for PPTP, which is one of the more popular configuration options."
And here: https://proxy.sh/panel/knowledgebase/246/PPTP-VPN-for-Google-Chrome-OS.html PPTP (VPN) for Google Chrome OS - Google Chrome OS does not support the PPTP protocol. It only supports L2TP and OpenVPN protocols. Please see the guide for L2TP here and the guide for OpenVPN here. Both these protocols are stronger in encryption than PPTP.
I am rather surprised that after all these years, people still think PPTP is a viable VPN option. Microsoft has continued to deny. And since PPTP is a much easier to use VPN technology than most of the others (handles NATs on both ends, can run through double-NATs, etc. while the others tend to be problematic in such common settings), it was arguably the most widely used VPN option, though as tools have become more robust for the other technologies, there has been some significant changes. I would never have guessed that as recently as 2014 my 2002 research would still be cited as relevant in the tech industry, and that the debate was still freshly ongoing in 2015!
Maybe I am reading more into this than is actually there? But if it did in any way help influence them, then I am glad my hours/weeks/months of research work helped protect at least a few people, and that at least one of the Google ChromeOS developers found my paper of value in standing up to what was probably considerable pressure to add a feature available in all the other operating systems.
Since Google has announced they plan to kill off Chrome OS and merge it with Android, will they throw aside the more security concious approach, and allow PPTP? I'll have to check into that and see. While I see there are many third party apps to use PPTP as a VPN protocol, I hope Google doesn't natively support PPTP (instead supporting the safer VPN protocols natively). It would be a shame if they caved to ignorant peer pressure for such a terribly insecure protocol.
And it is still very broken: https://www.schneier.com/blog/archives/2012/08/breaking_micros.html
UPDATE 20160803
Someone pointed out that many others of note have used my paper as reference on this topic. This Google advanced info search reveals a few.
Some of significant note kindly citing my research include:
- Chromium Dev Debate - https://bugs.chromium.org/p/chromium/issues/detail?id=207904
- FreedomHouse - https://freedomhouse.org/sites/default/files/Safety%20on%20the%20Line.pdf Section on PPTP p64
- Microsoft posts acknowledgement of the vulnerabilities TEN YEARS LATER! - https://technet.microsoft.com/library/security/2743314 - Microsoft's suggestion: "Or ... use a more secure VPN tunnel." (August 20, 2012).
- Microsoft implemented a KLUDGE workaround of adding yet another layer (PEAP) of encapsulation (TLS) as a workaround: https://support.microsoft.com/en-us/kb/2744850
References
Malware FAQ: Microsoft PPTP VPN (by Hawke Robinson) - "The best option would be to migrate away from PPTP to one of the other protocols such as IPSec."
https://productforums.google.com/forum/#!category-topic/chromebook-central/beta/I3Z8Qc_1UYE
http://www.omgchrome.com/chromebook-ready-vpn-options-to-protect-your-privacy/
https://support.google.com/chromebook/answer/1282338?hl=en
https://github.com/moxie0/chapcrack
http://www.onlinehashcrack.com/
http://www.h-online.com/security/features/A-death-blow-for-PPTP-1716768.html
http://www.livehacking.com/2012/08/02/cloudcracker-uses-custom-hardware-to-crack-any-vpn-or-wi-fi-ms-chapv2-based-password/ - "All users and providers of PPTP VPN solutions should immediately start migrating to a different VPN protocol. PPTP traffic should be considered unencrypted."
http://www.h-online.com/security/news/item/Microsoft-says-don-t-use-PPTP-and-MS-CHAP-1672257.html
https://twitter.com/hashtag/cloudcracker
https://chrome.googleblog.com/2016/05/the-google-play-store-coming-to.html
http://cryptography.randombit.narkive.com/ehrISIBz/ms-pptp-mppe-only-as-secure-as-single-des
http://arstechnica.com/security/2012/07/broken-microsoft-sheme-exposes-traffic/
http://www.blacksheepnetworks.com/security/resources/pentest/12299.html